Echo Show 5 not working.....
-
I posted more detail about my Docker image using macvlan on a Synology NAS here:
https://forum.monoclecam.com/topic/255/using-synology-surveillance-station-and-dockerHope it helps!
Thanks, Robert
-
@lux4rd0, to Robert’s point my config works because Amazon is expecting a valid certificate and 443 connection.
This is more an Amazon thing as I’ve got the same requirements on some other automation work I’ve written custom Alexa skills for. In each case 443 for any API connections is the go.
To your question, Robert, the Apache proxy works fine as from what I can see in the traffic it’s only accepting http connections to 443 and isn’t proxying the RTSP stream, which is going direct from the echo show to the internal server via the DNS rebind?
I’ve posted a pic of my config to demonstrate…
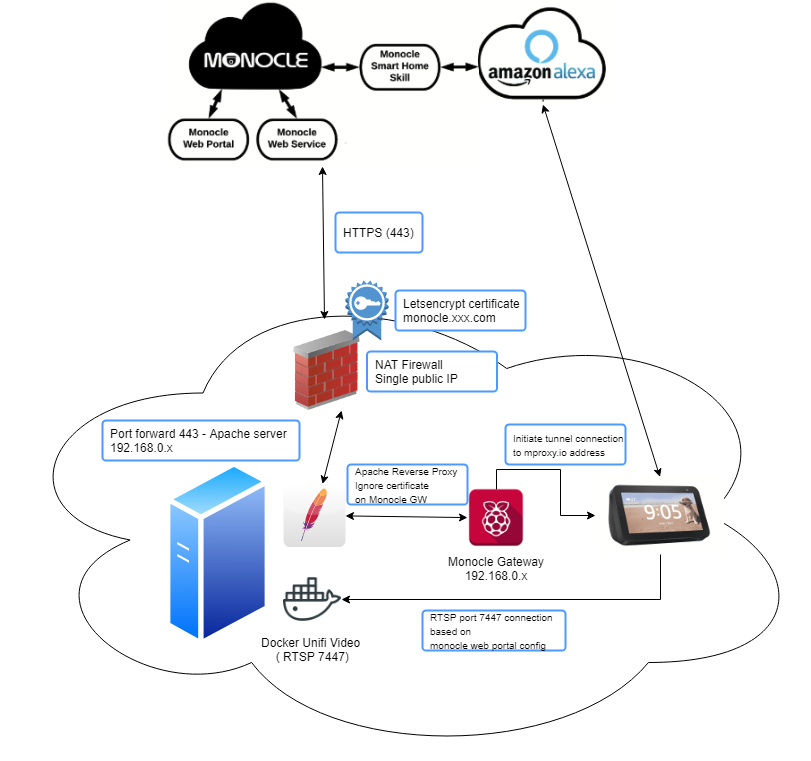
Apache proxy is working as per the above directives and using a virtual-host for the monocle.<myFQDN> and a valid certificate for that domain.
Either way this setup is functionally the same as docker and macvlan with the relevant work around to attach to my host’s network (as the docker container for unifi, and the apache server run on the same box.) You could do the same with VM’s as well if that’s your cup of tea.
At least this proves the following:
-
Apache Reverse proxy works (providing you use the directives I listed in my previous posts)
-
Docker macvlan can work, but just remember without working around the designed docker behaviour if your monocle gateway is trying to communicate with your RTSP server on the same IP as the host running Docker, it won’t work.
-
Unifi-Video RTSP streams on their weird port work, so the assumption there is that non-standard RTSP ports are ok.
-
Nothing is ever simple and I seem to find a way to complicate everything…
-
Me and Alexa are friends again.
-
-
@Monocle Have added the working reverse proxy conf for my setup in case it helps anyone as well:
#Virtual Host Setup in Apache as Monocle expects to use port 443 #This setup uses LetsEncrypt (https://letsencrypt.org/) and a dynamic DNS setup with a host entry for monocle #Either add to your apache conf file or create a new monocle.conf file and include that in the bottom of your apache conf. <VirtualHost *:443> ServerName monocle.<your FQDN here> SSLProxyEngine On SSLProxyCheckPeerName off SSLProxyCheckPeerExpire off SSLProxyCheckPeerCN off ProxyPreserveHost On ProxyRequests off ProxyPass / https://<address of monocle gateway>:443/ ProxyPassReverse / https://<address of monocle gateway>:443/ # Haven't tested if you need this for Monocle, but in prior experience not changing websocket traffic also plays havoc on API calls. I've left it in but remove # and experiment as you need. RewriteEngine on RewriteCond %{HTTP:Upgrade} =websocket [NC] RewriteRule /(.*) ws://<address of monocle gateway>:443/$1 [P,L] RewriteCond %{HTTP:Upgrade} !=websocket [NC] RewriteRule /(.*) https://address of monocle gateway>:443/$1 [P,L] # The below comes from letsencrypt and should be generated automatically if you follow the instructions on the letsencrypt web site # I've left this in to show where you'd put your certificate files SSLCertificateFile <path to your SSL cert file.pem> SSLCertificateKeyFile <path to your keyfile.pem> Include <your apache ssl conf file here> SSLCertificateChainFile <path to your ChainFile </VirtualHost> #Redirect anything to https <VirtualHost *:80> ServerName monocle.<your FQDN here> Redirect permanent / https://monocle.<your FQDN here>/ </VirtualHost> -
Thanks for all the details. I’m still sorting it all out in my head, but do have a couple of notes.
When using the Monocle Gateway with a camera that is tagged with any of these:
@tunnel,@proxyor@proxy-tcpthe RTSP stream is initiated from the Alexa device directly to the Monocle Gateway. Not directly to the camera or in your case the Docker Unifi Video server. (So it would be the Monocle Gateway that actually communicates RTSP to the Unifi server.)I see now that you are generating your own LetsEncrypt certificate and that is allowing you to terminate it on your Apache server. That makes sense now. Just a note, if you already have your own domain name and SSL certificate, you should be able to override the DNS hostname that Monocle Gateway uses. See the Monocle Gateway Configuration topic here. There is no magic here, you just need a publicly resolvable DNS host entry that points to an IP address where the Monocle Gateway is listening (or via Apache proxy in your case.)
I was under the impression that the RTSP protocol was not able to be proxied via an Apache or NGINX server. But I guess I got that wrong somewhere. Maybe the TCP only streams are OK, not sure it would work with UDP streams. I’ll have to play with this setup again when I have some time. The SSL termination could be difficult for some people, but for advanced users this could be a nice alternative.
You probably don’t need to worry about the proxy handling any web sockets, at least not at this time – that may change in the future as we plan on adding a Monocle Gateway Web GUI with access to logs, etc. Today only outbound secure web sockets are used to communicate with the Monocle servers over the Internet.
Thanks, Robert