Cannot get it Working :-(
-
Hi guys, running a Pi 3
with monocle gateway, 5 Hikvision cameras DS-2CD2135FWD-I
I can use VLC to see the RTSP feeds no issue

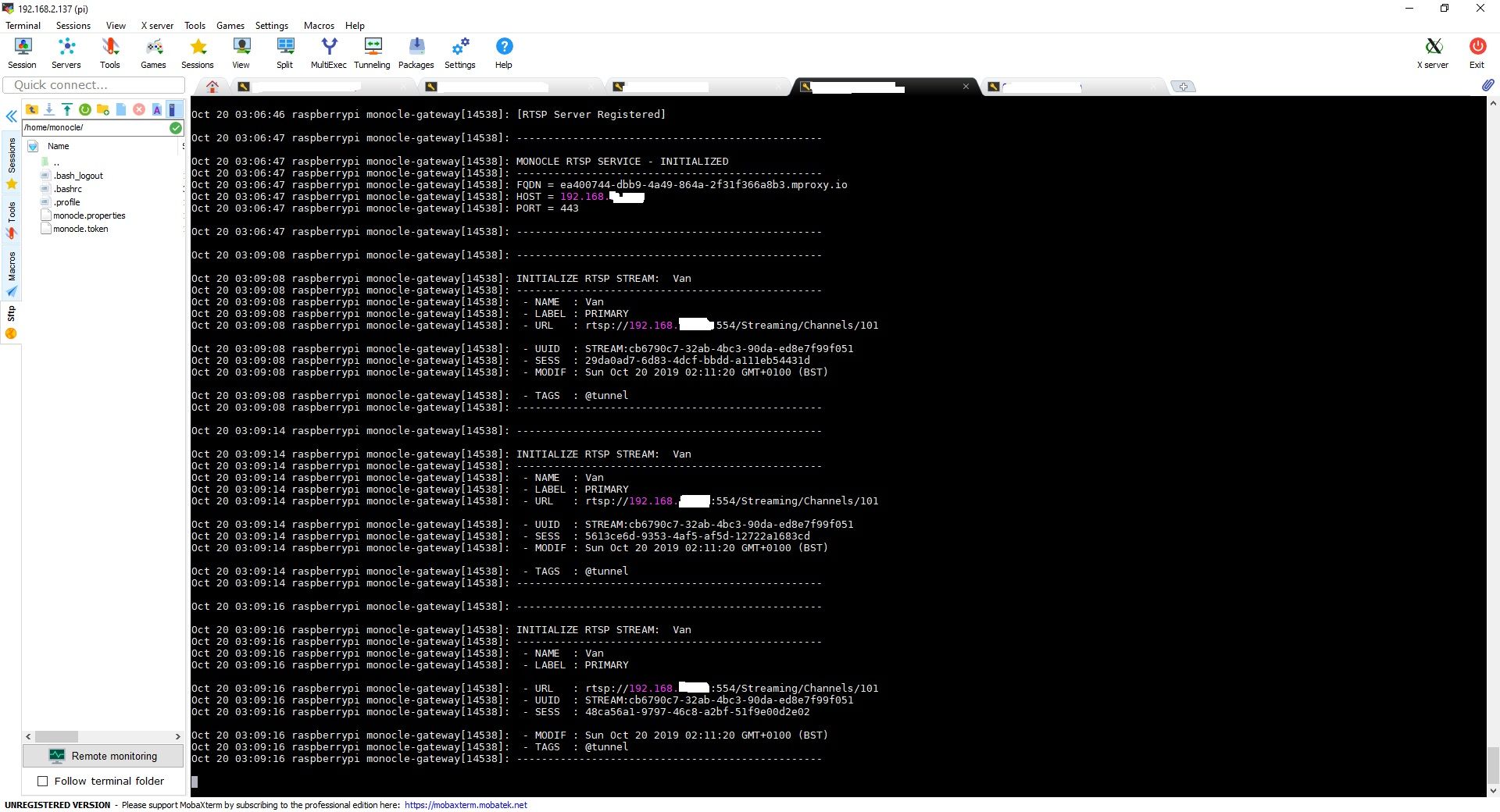
Attached are screenshots of Monocle running.
The only thing I can think and have no idea how to resolve is the DNS Binding
If I ping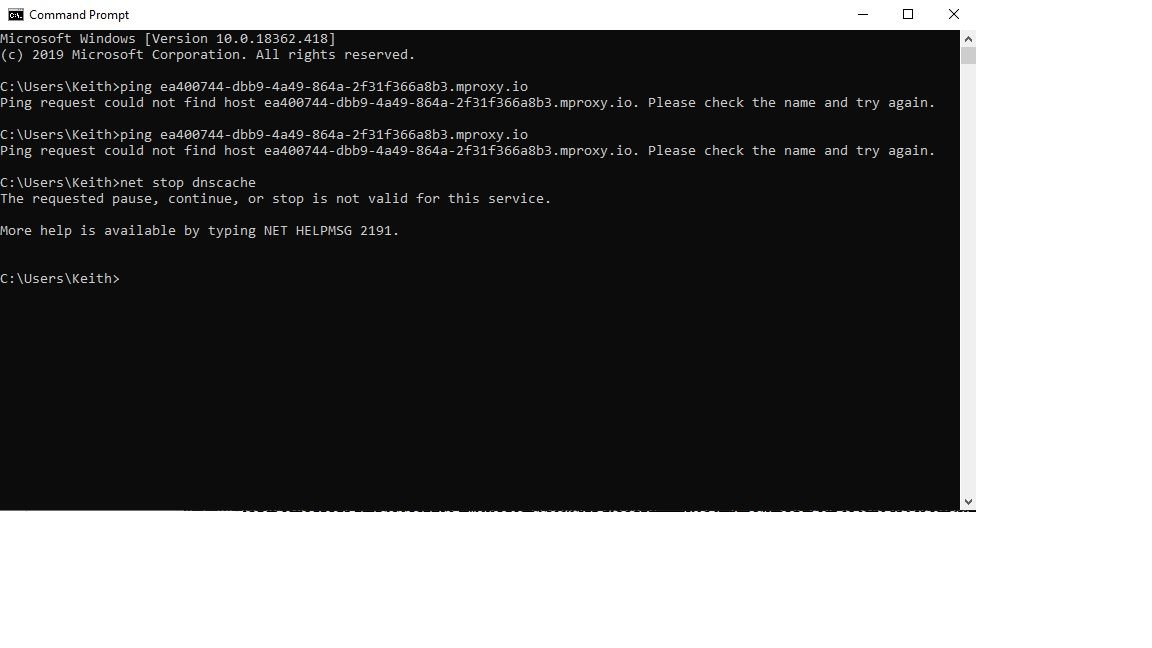
Im in the UK and running an EE standard router Bright Box 1, I cannot see anywhere where it mentions DNS Binding.
Any help appreciated
-
Definitely looks like a DNS rebinding issue based on the log data and on your
pingattempts.The
pingattempts should resolve the DNS hostname to the local IP address of your monocle gateway instance:192.168.?.?.I’m not familiar with Bright Box routers, but you may check with the manufacturer or some online forums for this hardware to see if there is a way to allow a specific hostname (your Monocle FQDN) to bypass the DNS rebinding blocking.
An alternative option if your router allows for it is to configure/map a static DNS hostname (your Monocle FQDN) in your router’s DNS server to always resolve to the IP address where the monocle gateway is running.
-
Thankyou i’ll give it a go cheers
-
Right, still struggling.
I have a Draytek Vigor Router now, old but solid. I can now resolve the mproxy.io
and port 443 is open and forwarded to my Monocle server (Checked on Open port Checker)
I can see my camera in VLC
And all I get from Alexa is Hmmmmmmm the camera is not responding… Liar liar I end up shouting :-)Any help appreciated
-
@Alarm_guy1 said in Cannot get it Working :-(:
And all I get from Alexa is Hmmmmmmm the camera is not responding… Liar liar I end up shouting
Any help appreciatedGo ahead and post the text log from the Monocle Gateway that captures your request for a single camera view attempt. Let’s see how far its getting no in the process with the DNS issue resolved.
Thanks, Robert
-
Personally I gave up on the proxy solution, and setup an instance of stunnel and got my own domain pointing to it with a free SSL cert that i renew every so often.
It works brilliantly. Sure you have to screw around with port forwarding on your router, but i could never get the proxy to connect, whereas a simple ssl tunnel worked just fine. I still use the monocle cam skill and service which is actually very nice and works 100% of the time.
-
The proxy solution does work for a large number of users. It does have certain complications under some networking environments that can cause additional headaches. However …
Yes running your own SSL tunneled connection (stunnel) with valid SSL certificates against a publicly resolvable DNS hostname is perfectly fine. Obviously this requires an advanced skillset and does force you to expose your camera feed on an open port to the Internet. But I’m sure with your skillset you are comfortable with how you handle the security to access your camera feed.
Thanks, Robert
-
Cheers Zyrorl, but a bit out of my league.
my log frompi@raspberrypi:~ $ monocle-gateway --tail ****************************************************************** * __ __ ___ _ _ ___ ___ _ ___ * * | \/ |/ _ \| \| |/ _ \ / __| | | __| * * | |\/| | (_) | .` | (_) | (__| |__| _| * * |_| |_|\___/|_|\_|\___/ \___|____|___| * * * ****************************************************************** <<TAIL>> LOG FOR THE [MONOCLE-GATEWAY] SERVICE -- Logs begin at Thu 2016-11-03 17:16:43 GMT. -- Oct 29 00:00:18 raspberrypi systemd[1]: Started Monocle Gateway Service. Oct 29 00:00:24 raspberrypi monocle-gateway[511]: ****************************************************************** Oct 29 00:00:24 raspberrypi monocle-gateway[511]: * __ __ ___ _ _ ___ ___ _ ___ * Oct 29 00:00:24 raspberrypi monocle-gateway[511]: * | \/ |/ _ \| \| |/ _ \ / __| | | __| * Oct 29 00:00:24 raspberrypi monocle-gateway[511]: * | |\/| | (_) | .` | (_) | (__| |__| _| * Oct 29 00:00:24 raspberrypi monocle-gateway[511]: * |_| |_|\___/|_|\_|\___/ \___|____|___| * Oct 29 00:00:24 raspberrypi monocle-gateway[511]: * * Oct 29 00:00:24 raspberrypi monocle-gateway[511]: ****************************************************************** Oct 29 00:00:28 raspberrypi monocle-gateway[511]: ------------------------------------------------- Oct 29 00:00:28 raspberrypi monocle-gateway[511]: MONOCLE RUNTIME ENVIRONMENT Oct 29 00:00:28 raspberrypi monocle-gateway[511]: ------------------------------------------------- Oct 29 00:00:28 raspberrypi monocle-gateway[511]: VERSION = 0.0.4 Oct 29 00:00:28 raspberrypi monocle-gateway[511]: OS/ARCH = linux/arm Oct 29 00:00:28 raspberrypi monocle-gateway[511]: PROCESS = monocle-gateway (PID=511) Oct 29 00:00:28 raspberrypi monocle-gateway[511]: TIMESTAMP = 2019-10-29T00:00:28.763Z Oct 29 00:00:28 raspberrypi monocle-gateway[511]: ------------------------------------------------- Oct 29 00:00:28 raspberrypi monocle-gateway[511]: MONOCLE GATEWAY SERVICE (Version: 0.0.4) Oct 29 00:00:28 raspberrypi monocle-gateway[511]: ------------------------------------------------- Oct 29 00:00:28 raspberrypi monocle-gateway[511]: [Monocle Starting] Oct 29 00:00:28 raspberrypi monocle-gateway[511]: [Monocle Connecting] Oct 29 00:00:29 raspberrypi monocle-gateway[511]: [Monocle Started] Oct 29 00:00:29 raspberrypi monocle-gateway[511]: [RTSP Server Starting] Oct 29 00:00:29 raspberrypi monocle-gateway[511]: [RTSP Server Listening] 0.0.0.0:8555 (RTSP) Oct 29 00:00:29 raspberrypi monocle-gateway[511]: [RTSP Server Listening] 0.0.0.0:443 (RTSP-TLS) Oct 29 00:00:29 raspberrypi monocle-gateway[511]: [RTSP Proxy Started] (PID=854) Oct 29 00:00:29 raspberrypi monocle-gateway[511]: [RTSP Server Listening] 0.0.0.0:8554 (PROXY) Oct 29 00:00:29 raspberrypi monocle-gateway[511]: [RTSP Server Started] Oct 29 00:00:29 raspberrypi monocle-gateway[511]: [Monocle Connected] Oct 29 00:00:29 raspberrypi monocle-gateway[511]: [RTSP Server Registered] Oct 29 00:00:29 raspberrypi monocle-gateway[511]: ------------------------------------------------- Oct 29 00:00:29 raspberrypi monocle-gateway[511]: MONOCLE RTSP SERVICE - INITIALIZED Oct 29 00:00:29 raspberrypi monocle-gateway[511]: ------------------------------------------------- Oct 29 00:00:29 raspberrypi monocle-gateway[511]: FQDN = ea400744-dbb9-4a49-864a-2f31f366xxxx.mproxy.io Oct 29 00:00:29 raspberrypi monocle-gateway[511]: HOST = 192.168.x.xxx Oct 29 00:00:29 raspberrypi monocle-gateway[511]: PORT = 443 Oct 29 00:00:29 raspberrypi monocle-gateway[511]: ------------------------------------------------- Oct 29 01:55:19 raspberrypi monocle-gateway[511]: ------------------------------------------------- Oct 29 01:55:19 raspberrypi monocle-gateway[511]: INITIALIZE RTSP STREAM: Front Garden Oct 29 01:55:19 raspberrypi monocle-gateway[511]: ------------------------------------------------- Oct 29 01:55:19 raspberrypi monocle-gateway[511]: - NAME : Front Garden Oct 29 01:55:19 raspberrypi monocle-gateway[511]: - LABEL : PRIMARY Oct 29 01:55:19 raspberrypi monocle-gateway[511]: - URL : rtsp://192.168.x.xxx:554/ch1/main/av_stream Oct 29 01:55:19 raspberrypi monocle-gateway[511]: - UUID : STREAM:00f320ea-8719-4a06-9200-2867184bxxxx Oct 29 01:55:19 raspberrypi monocle-gateway[511]: - SESS : 05149b83-87b7-4be2-a779-e534685fxxxx Oct 29 01:55:19 raspberrypi monocle-gateway[511]: - MODIF : Mon Oct 28 2019 20:09:10 GMT+0000 (GMT) Oct 29 01:55:19 raspberrypi monocle-gateway[511]: - TAGS : @tunnel Oct 29 01:55:19 raspberrypi monocle-gateway[511]: ------------------------------------------------- Oct 29 01:55:22 raspberrypi monocle-gateway[511]: ------------------------------------------------- -
Based on the log the gateway is still not receiving inbound requests from Alexa.
From another computer (not the gateway) try to perform a NSLOOKUP command using the FQDN (
ea400744-dbb9-4a49-864a-2f31f366xxxx.mproxy.io)nslookup ea400744-dbb9-4a49-864a-2f31f366xxxx.mproxy.ioIt should resolve to your private IP address where the gateway is running inside your network.
Is the HOST address (
192.168.x.x) reported at the beginning of the log the correct IP address for this machine? The Monocle Gateway will attempt to automatically detect the IP address but sometimes if there are multiple addresses associated to the computer, it can assign the wrong one.Are the Alexa devices are the same network as the Monocle Gateway … meaning they are not on a Guest WiFi network or isolated VLAN? The Alexa devices will need to communicate directly with the gateway on the local network.
Thanks, Robert
-
@Alarm_guy1 said in Cannot get it Working :-(:
and port 443 is open and forwarded to my Monocle server (Checked on Open port Checker)
PS … port 443 does not need to be exposed to the Internet and thus does not require port forwarding when using the Monocle Gateway. Port 443 does need to be accessible on the local network so it should not be blocked by any firewall or in use by another service/software on the machine running the Monocle Gateway.
-
@Monocle Actually just to be clear this isn’t actually
@Monocle said in Cannot get it Working :-(:
@zyrorl
Yes running your own SSL tunneled connection (stunnel) with valid SSL certificates against a publicly resolvable DNS hostname is perfectly fine. Obviously this requires an advanced skillset and does force you to expose your camera feed on an open port to the Internet. But I’m sure with your skillset you are comfortable with how you handle the security to access your camera feed.Just to be clear this is not at all true. I have managed to get it working just fine at least with Alexa on both the latest Generation Fire TV Stick 4k, second generation FireTV stick, and Fire TV 4k 2nd Edition.
You do not need to expose your camera feed on the internet, nor open any ports whatsoever. All you do need to do, is make sure your devices are on the same network as your camera ips, and make sure your DNS does resolve to a local internal IP address. For example
cctv.zyrorl.compoints to192.168.1.102, which is not accessible to the internet, but is accessible to the Fire TV devices. Getting valid ssl certificates is certainly not difficult (with letsencrypt), and getting publically resolvable dns is pretty much free if you just go with any of the dynamic dns outfits, or purchase your own domain.So I don’t need to open any ports whatsoever, best thing is the Fire TV devices aren’t traversing the internet to connect to the cameras either.
My
stunnel.conffile looks like this:foreground=yes debug=5 pid = /var/run/stunnel.pid syslog=yes output=stunnel [rtsp] accept = 192.168.1.102:443 # Local IP address to listen connect = 192.168.1.140:554 # CCTV NVR box cert = /etc/stunnel/cctv.zyrorl.com.pem # your certificateThen on my monocle configuration:
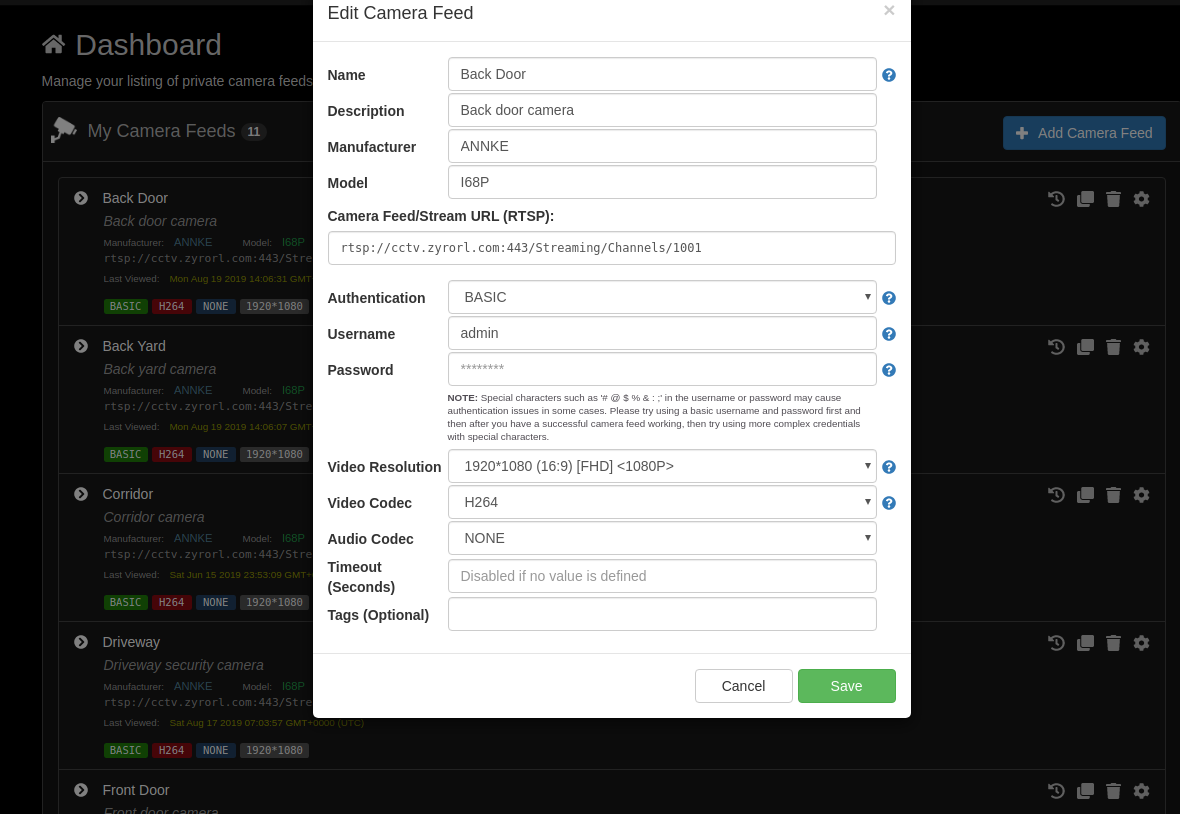
This works entirely without exposing any of my cameras to the internet (hence i’m so comfortable posting the actual addresses because they resolve to local ip addresses). No port forwards required.
-
You are correct about the ability to use a private IP address for your SSL termination!
Thanks, Robert
-
I’m still strugggling, but not is a position to keep trying atm but will come back to this soon
cheers -
@Monocle It might be an alternative methods to expose these cameras for certain setups. Thanks for producing such a great and high quality service. :) I have donated to you guys :)
-
Thank you for your donation! Glad its working well for your situation/environment.
-
@Monocle said in Cannot get it Working :-(:
@Alarm_guy1
Based on the log the gateway is still not receiving inbound requests from Alexa.
From another computer (not the gateway) try to perform a NSLOOKUP command using the FQDN (ea400744-dbb9-4a49-864a-2f31f366xxxx.mproxy.io)
nslookup ea400744-dbb9-4a49-864a-2f31f366xxxx.mproxy.ioIt should resolve to your private IP address where the gateway is running inside your network.
Is the HOST address (192.168.x.x) reported at the beginning of the log the correct IP address for this machine? The Monocle Gateway will attempt to automatically detect the IP address but sometimes if there are multiple addresses associated to the computer, it can assign the wrong one.
Are the Alexa devices are the same network as the Monocle Gateway … meaning they are not on a Guest WiFi network or isolated VLAN? The Alexa devices will need to communicate directly with the gateway on the local network.
Thanks, RobertRight back on this for today anyway:
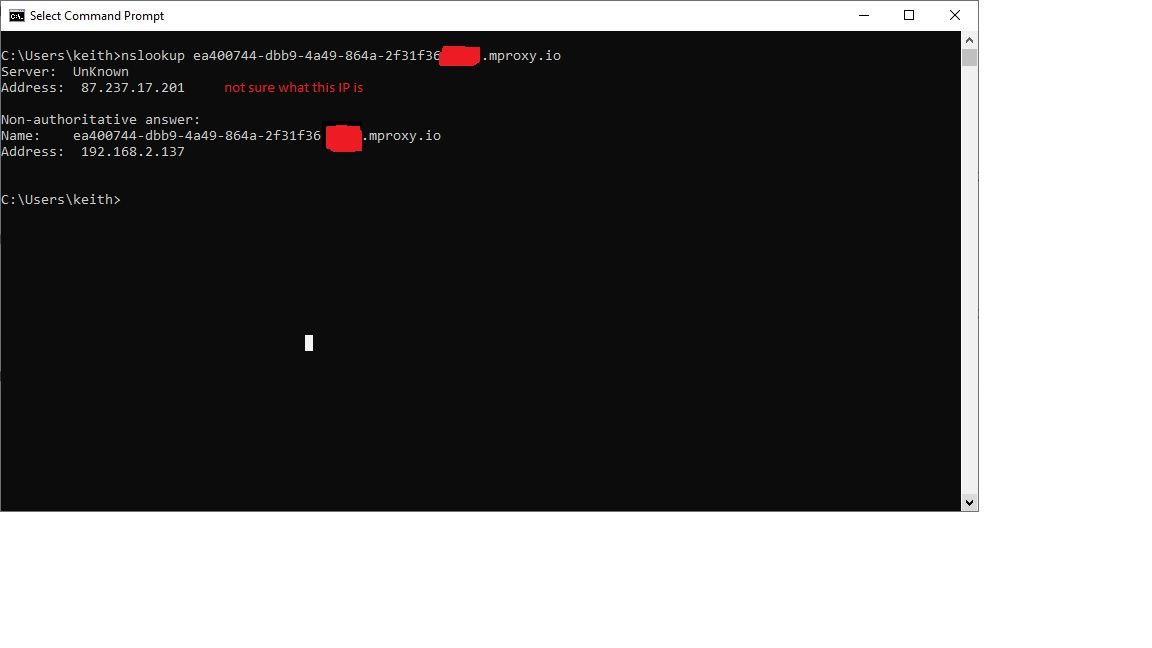
The nslookup results posted.
The only issue I think is I have a Ubiquity Unifi WiFi extender but the as my router now doesnt have built in WiFi.
the Pi that monocle is on is hardwired into a switch that is connected to the switch that the Unifi is connected to…it would be good to get this going :-)
cheers for the continued help