Hikvision DB1 (WiFi Video Doorbell)
-
If you would like to temporarily expose your camera feed to us, we could test our current fix and see if its working for this newer model as well. Just open a support ticket and we can test it this coming week.
Thanks, Robert
-
Very interested in this too. Let me know if I can help testing to making it work.
-
Any update on this?
-
We have working prototype code that appears to work with this camera, but it’s not complete nor integrated into the Monocle Gateway software yet.
-
When do you plan on completion/integration?
-
This is slated for the next release version of Monocle Gateway. So probably a month or two out at this point. Once we have it ready for testing, we can provide an early access copy for you to try out. Thanks, Robert
-
@Monocle
Glad to hear! I’m also interested. Please let me know when available and if you need help testing. -
Count me in to help test as well. I have a RCA HSDB1 doorbell cam and a new Echo Show 5. I run the gateway in a docker container so its easy for me to test it if you need another tester.
-
Just noticed these posts.
Here also purchased a Hikvision OEM DB2 WiFi Video Doorbell.
I can stream main and sub streams:
rxxp://192.168.1.100:554/user=admin_password=password_channel=0_stream=0.sdp ==> 1536X2048
rxxp://user:[email protected]:554/ch1/sub/av_stream ==> 384X512
Use ONVIF (no passwords) for main stream:
rxxp://192.168.1.100:554/onvif
Use JPG capture for main stream.
hxxp://192.168.1.100/onvif/snapshot.jpg
There are a few folks now purchasing the new DB2 doorbell cameras. None are sold here in the US by Hikvision. The are sold labeless or under RCA or EZViz.
I just switched over from Ring to this one. I am very impressed with it.
Please let me know what I can do helping to get this video doorbell in the database.
-
I have this doorbell and have tried everything, every possible combination and have not been able to have it stream to the Echo Show.
I saw on an earlier post about sharing the stream, I can do this if anyone wants to troubleshoot the problem
-
@jackofallsorts said in Hikvision DB1 (WiFi Video Doorbell):
I have this doorbell and have tried everything, every possible combination and have not been able to have it stream to the Echo Show.
I saw on an earlier post about sharing the stream, I can do this if anyone wants to troubleshoot the problem
Robert from Monocle gave me a beta to test with. It sort of worked but how I wanted it to work. In this particular camera Hikvision responds with some weird response to SDP Audio. It sends an empty response to the sprop command. Robert provided me with a pre-beta of 0.0.4 that sort of fixed the issue and it worked, but only with no audio. My ticket was 3417. Maybe he will share that code for you all to try. I don’t want to share it because I don’t think it was meant for public release.
-
Just tried this again with @gateway @proxy with DB2 and still no luck.
-
@redcaesar said in Hikvision DB1 (WiFi Video Doorbell):
Just tried this again with @gateway @proxy with DB2 and still no luck.
Try adding @fakefmtp to the Tags section. This worked for me. It does seem to be a little slower bringing up the camera compared to other Hikvision cameras I have, but it does work. I have tested this on the Nelly NSC-DB2 and the Hikvision DS-HD1 doorbell cameras.
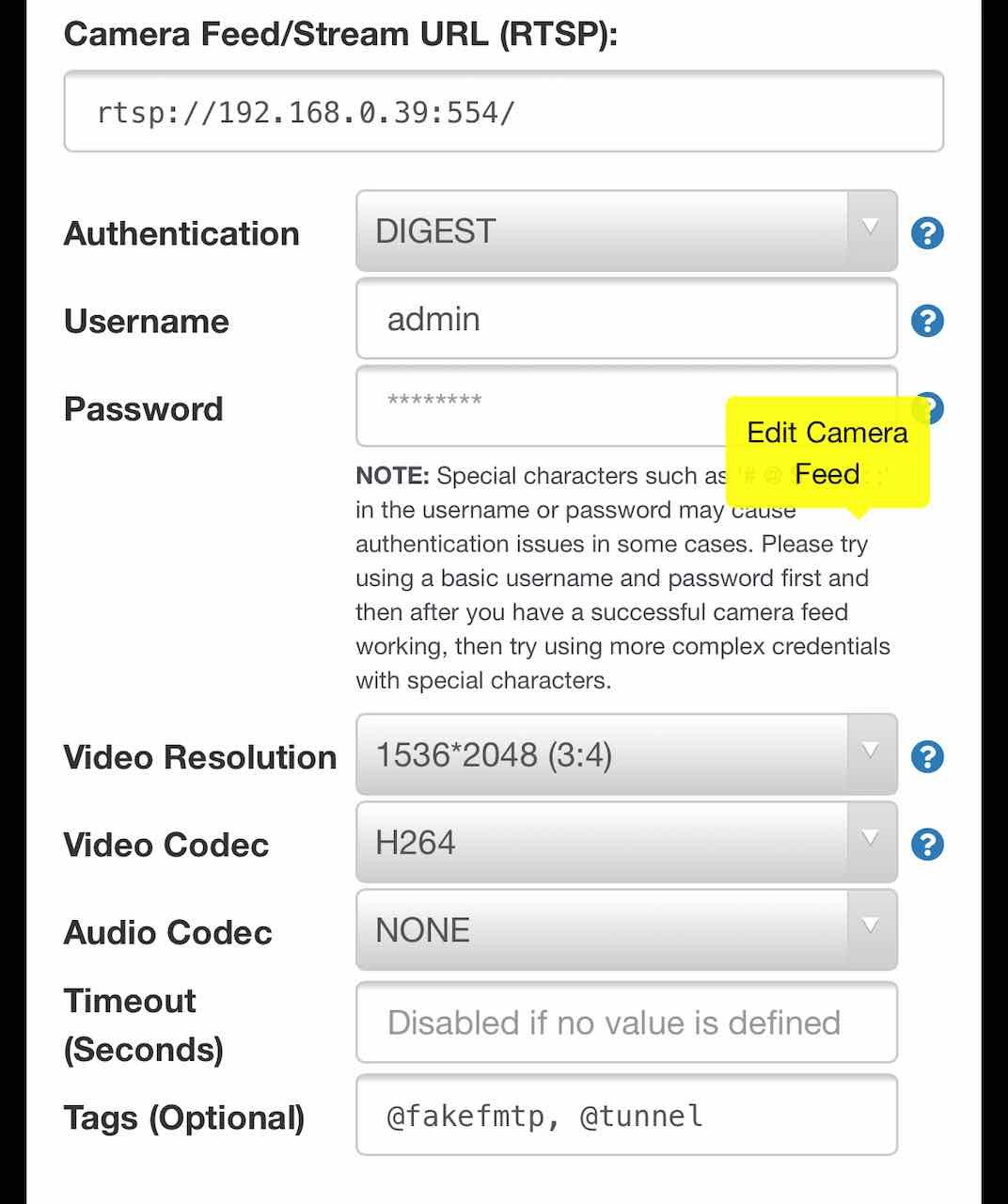
-
Great news Scott!!! I did not know that @ fakefmtp was an option for the proxy.
Works fine.
Tried the audio and it is not working at this time…Just purchased the DB1 EU version of the doorbell. Not as nice of specs as the DB2 but the firmware is totally open for use. IE: RTSP, ONVIF, JPG and it appears to have a web interface. So want to see how this one ones with Monocle. I had no issues with tested Hikvision 5MP camera boards.
-
@pete @ScottR-LA Finally the connection works with @fakefmtp tag, I see a black screen but I can hear the audio on my Amazon Echo Show 8 device. But it’s a step ahead, at least I know connection was not a problem.
UPDATE: On Echo Show 5 device (the smaller ones) both video and audio work fine. So it’s just a problem with Echo Show 8, the one with the bigger screen.
I have an EZVIZ DB1 with monocle gateway on a synology, via docker. With the EZVIZ skill video&audio are ok on all Alexa devices, Echo Show 5 and Echo Show 8. With Monocle only Echo Show 5 works fine, on the 8 I can only hear audio.
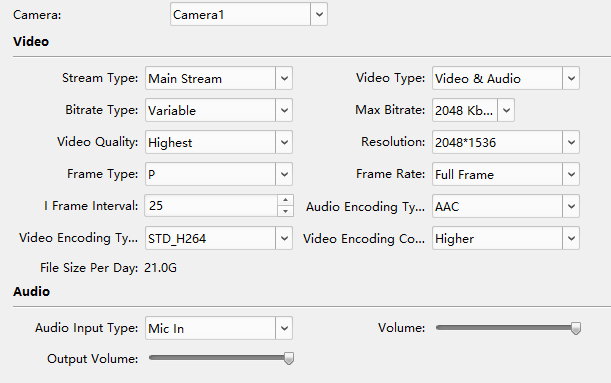
Question: resolution: 2048x1536 or 1536x2048? On Hikvision Config tool I see the former (2048*1536).
Thanks.
-
@alexdelprete , @pete , @ScottR-LA
No luck for me using the Hikvision DB1 model (Uniden branded).
I get this error in the Monocle Gateway log:2020-01-22T20:01:34.561Z [DEBUG] [10.1.2.232:59095 <SJ8XqmIbL>] [ENDPOINT RESPONSE] <-- [405 (Method Not Allowed)] <cseq=1> (session=undefined) 2020-01-22T20:01:34.561Z [TRACE] [10.1.2.232:59095 <SJ8XqmIbL>] [ENDPOINT RESPONSE] <-- [HEADERS] {I’m running firmware: v1.4.64 build 180515.
I can access the RTSP stream just fine using FFMPEG/FFPLAY and VLC. Something incompatible in the RTSP layer between this camera and the gateway.
-
@ScottR-LA Wow that did the trick. Just got home and tested it and works. :grin: I changed settings to add @fakefmtp and changed audio and resolution as noted above.
Any way of speeding up the connection? Takes good 10 seconds to show live feed.
Here is a video of it working
Thanks
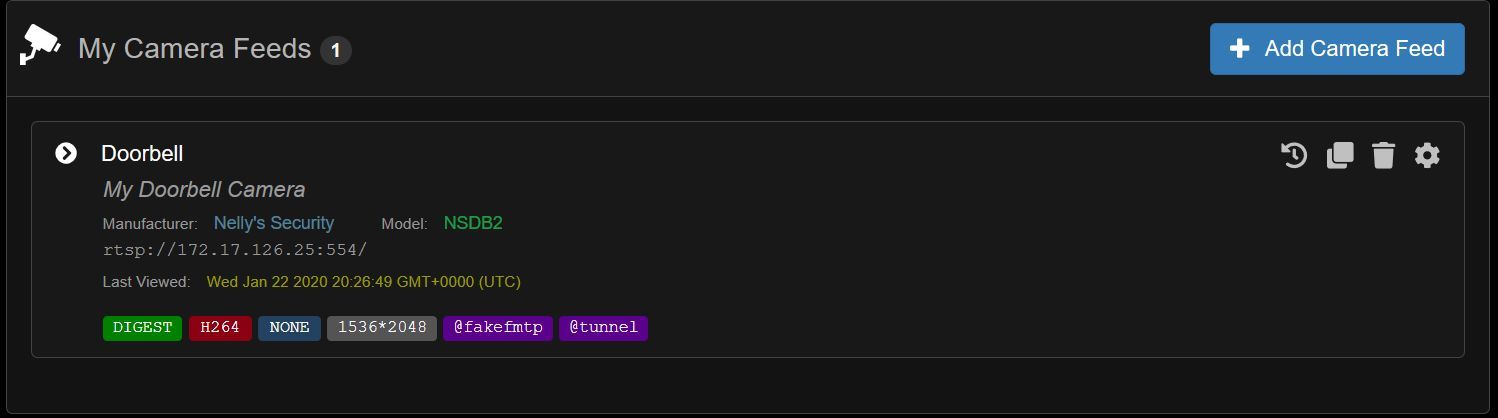
And gateway log if it is of any use.
****************************************************************** * __ __ ___ _ _ ___ ___ _ ___ * * | \/ |/ _ \| \| |/ _ \ / __| | | __| * * | |\/| | (_) | .` | (_) | (__| |__| _| * * |_| |_|\___/|_|\_|\___/ \___|____|___| * * * ****************************************************************** ------------------------------------------------- MONOCLE RUNTIME ENVIRONMENT ------------------------------------------------- VERSION = 0.0.4 OS/ARCH = win32\x64 PROCESS = monocle-gateway (PID=61204) TIMESTAMP = 2020-01-22T20:43:19.635Z ------------------------------------------------- MONOCLE GATEWAY SERVICE (Version: 0.0.4) ------------------------------------------------- [Monocle Starting] [Monocle Connecting] [Monocle Started] [RTSP Server Starting] [RTSP Server Listening] 0.0.0.0:8555 (RTSP) [RTSP Server Listening] 0.0.0.0:443 (RTSP-TLS) [RTSP Proxy Started] (PID=62096) [RTSP Server Listening] 0.0.0.0:8554 (PROXY) [RTSP Server Started] [Monocle Connected] [RTSP Server Registered] ------------------------------------------------- MONOCLE RTSP SERVICE - INITIALIZED ------------------------------------------------- FQDN = 0ff172e6-8e67-49e8-8432-a666fb929ddd.mproxy.io HOST = 172.17.126.11 PORT = 443 ------------------------------------------------- ------------------------------------------------- INITIALIZE RTSP STREAM: Doorbell ------------------------------------------------- - NAME : Doorbell - LABEL : PRIMARY - URL : rtsp://172.17.126.25:554/ - UUID : STREAM:314be7ee-cb79-440a-8b73-558d4d9e3c36 - SESS : 5ac6c1d6-e5e3-4993-9df0-094a9214618d - MODIF : Wed Jan 22 2020 15:30:54 GMT-0500 (Eastern Standard Time) - TAGS : @fakefmtp,@tunnel ------------------------------------------------- 2020-01-22T20:43:45.143Z [INFO] [172.17.126.58:46646 <HJK-NVLWI>] RTSP CLIENT SOCKET CONNECTED 2020-01-22T20:43:45.264Z [INFO] [172.17.126.58:46646 <HJK-NVLWI>] RTSP CLIENT ATTACHED TO STREAM: Doorbell (STREAM:314be7ee-cb79-440a-8b73-558d4d9e3c36) 2020-01-22T20:43:45.280Z [INFO] [172.17.126.58:46646 <HJK-NVLWI>] RTSP ENDPOINT SOCKET CONNECTED {172.17.126.25:554} 2020-01-22T20:43:45.284Z [DEBUG] [172.17.126.58:46646 <HJK-NVLWI>] [CLIENT REQUEST] --> [DESCRIBE] rtsp://0ff172e6-8e67-49e8-8432-a666fb929ddd.mproxy.io:443/STREAM:314be7ee-cb79-440a-8b73-558d4d9e3c36?session=5ac6c1d6-e5e3-4993-9df0-094a9214618d 2020-01-22T20:43:45.285Z [TRACE] [172.17.126.58:46646 <HJK-NVLWI>] [CLIENT REQUEST] --> [HEADERS] { "accept": "application/sdp", "user-agent": "Fire OS/6.0 stagefright/1.2 (Linux;Android 7.1.2)", "cseq": "1" } 2020-01-22T20:43:45.291Z [DEBUG] [172.17.126.58:46646 <HJK-NVLWI>] [ENDPOINT REQUEST] --> [DESCRIBE] rtsp://172.17.126.25:554/ 2020-01-22T20:43:45.297Z [TRACE] [172.17.126.58:46646 <HJK-NVLWI>] [ENDPOINT REQUEST] --> [HEADERS] { "accept": "application/sdp", "user-agent": "Fire OS/6.0 stagefright/1.2 (Linux;Android 7.1.2)", "cseq": "1" } 2020-01-22T20:43:45.446Z [DEBUG] [172.17.126.58:46646 <HJK-NVLWI>] [ENDPOINT RESPONSE] <-- [401 (Unauthorized)] <cseq=1> (session=undefined) 2020-01-22T20:43:45.450Z [TRACE] [172.17.126.58:46646 <HJK-NVLWI>] [ENDPOINT RESPONSE] <-- [HEADERS] { "cseq": "1", "www-authenticate": "Digest realm=\"f84dfc9a436b\", nonce=\"9a262528de6debf634b0858eec3f13bc\", stale=\"FALSE\", Basic realm=\"f84dfc9a436b\"", "date": "Sat, Jan 18 2020 01:43:28 GMT" } 2020-01-22T20:43:45.455Z [INFO] [172.17.126.58:46646 <HJK-NVLWI>] RTSP ENDPOINT REQUIRES AUTHENTICATION: Digest realm="f84dfc9a436b", nonce="9a262528de6debf634b0858eec3f13bc", stale="FALSE", Basic realm="f84dfc9a436b" 2020-01-22T20:43:45.458Z [INFO] [172.17.126.58:46646 <HJK-NVLWI>] RTSP ENDPOINT ATTEMPTING AUTHENTICATION: DIGEST 2020-01-22T20:43:45.463Z [DEBUG] [172.17.126.58:46646 <HJK-NVLWI>] [ENDPOINT REQUEST] --> [DESCRIBE] rtsp://172.17.126.25:554/ 2020-01-22T20:43:45.465Z [TRACE] [172.17.126.58:46646 <HJK-NVLWI>] [ENDPOINT REQUEST] --> [HEADERS] { "accept": "application/sdp", "user-agent": "Fire OS/6.0 stagefright/1.2 (Linux;Android 7.1.2)", "cseq": "1", "authorization": "Digest username=\"admin\", realm=\"f84dfc9a436b\", nonce=\"9a262528de6debf634b0858eec3f13bc\", uri=\"rtsp://172.17.126.25:554/\", response=\"4691f39f5927c8f5edacd750bc1b42c2\"" } 2020-01-22T20:43:45.843Z [DEBUG] [172.17.126.58:46646 <HJK-NVLWI>] [ENDPOINT RESPONSE] <-- [200 (OK)] <cseq=1> (session=undefined) 2020-01-22T20:43:45.844Z [TRACE] [172.17.126.58:46646 <HJK-NVLWI>] [ENDPOINT RESPONSE] <-- [HEADERS] { "cseq": "1", "content-type": "application/sdp", "content-base": "rtsp://172.17.126.25:554/", "content-length": "459" } 2020-01-22T20:43:45.849Z [TRACE] [172.17.126.58:46646 <HJK-NVLWI>] [ENDPOINT RESPONSE] <-- [BODY] v=0 o=- 1579311809203418 1579311809203418 IN IP4 172.17.126.25 s=Media Presentation e=NONE b=AS:5050 t=0 0 a=control:rtsp://172.17.126.25:554/ m=video 0 RTP/AVP 96 b=AS:5000 a=control:rtsp://172.17.126.25:554/trackID=1 a=rtpmap:96 H264/90000 a=fmtp:96 profile-level-id=420029; packetization-mode=1; sprop-parameter-sets= a=Media_header:MEDIAINFO=494D4B48010100000400010000000000000000000000000000000000000000000000000000000000; a=appversion:1.0 2020-01-22T20:43:45.853Z [INFO] [172.17.126.58:46646 <HJK-NVLWI>] RTSP ENDPOINT AUTHENTICATION SUCCESSFUL: DIGEST 2020-01-22T20:43:45.857Z [INFO] [172.17.126.58:46646 <HJK-NVLWI>] RTSP ENDPOINT SDP VIDEO FMTP MODIFIED 2020-01-22T20:43:45.866Z [DEBUG] [172.17.126.58:46646 <HJK-NVLWI>] [CLIENT RESPONSE] <-- [200 (OK)] <cseq=1> (session=undefined) 2020-01-22T20:43:45.873Z [TRACE] [172.17.126.58:46646 <HJK-NVLWI>] [CLIENT RESPONSE] <-- [HEADERS] { "cseq": "1", "content-type": "application/sdp", "content-base": "rtsp://172.17.126.25:554/", "content-length": "528" } 2020-01-22T20:43:45.877Z [TRACE] [172.17.126.58:46646 <HJK-NVLWI>] [CLIENT RESPONSE] <-- [BODY] v=0 o=- 1579311809203418 1579311809203418 IN IP4 172.17.126.25 s=Media Presentation b=AS:5050 t=0 0 a=control:rtsp://172.17.126.25:554/ m=video 0 RTP/AVP 96 b=AS:5000 a=rtpmap:96 H264/90000 a=fmtp:96 profile-level-id=420029; packetization-mode=1; sprop-parameter-sets=Z00AKZpnA8ARPy4C1AQEBQAAAwPoAADqYOhgACZJQAAJkkK7y40MAATJKAABMkhXeXCg,aO48gA== a=control:rtsp://172.17.126.25:554/trackID=1 a=Media_header:MEDIAINFO=494D4B48010100000400010000000000000000000000000000000000000000000000000000000000; a=appversion:1.0 2020-01-22T20:43:45.902Z [DEBUG] [172.17.126.58:46646 <HJK-NVLWI>] [CLIENT REQUEST] --> [SETUP] rtsp://172.17.126.25:554/trackID=1 2020-01-22T20:43:45.905Z [TRACE] [172.17.126.58:46646 <HJK-NVLWI>] [CLIENT REQUEST] --> [HEADERS] { "transport": "RTP/AVP/TCP;interleaved=0-1", "user-agent": "Fire OS/6.0 stagefright/1.2 (Linux;Android 7.1.2)", "cseq": "2" } 2020-01-22T20:43:45.917Z [DEBUG] [172.17.126.58:46646 <HJK-NVLWI>] [ENDPOINT REQUEST] --> [SETUP] rtsp://172.17.126.25:554/trackID=1 2020-01-22T20:43:45.919Z [TRACE] [172.17.126.58:46646 <HJK-NVLWI>] [ENDPOINT REQUEST] --> [HEADERS] { "transport": "RTP/AVP/TCP;interleaved=0-1", "user-agent": "Fire OS/6.0 stagefright/1.2 (Linux;Android 7.1.2)", "cseq": "2", "authorization": "Digest username=\"admin\", realm=\"f84dfc9a436b\", nonce=\"9a262528de6debf634b0858eec3f13bc\", uri=\"rtsp://172.17.126.25:554/\", response=\"4691f39f5927c8f5edacd750bc1b42c2\"" } 2020-01-22T20:43:46.277Z [DEBUG] [172.17.126.58:46646 <HJK-NVLWI>] [ENDPOINT RESPONSE] <-- [200 (OK)] <cseq=2> (session=1653669771;timeout=20) 2020-01-22T20:43:46.280Z [TRACE] [172.17.126.58:46646 <HJK-NVLWI>] [ENDPOINT RESPONSE] <-- [HEADERS] { "cseq": "2", "session": "1653669771;timeout=20", "transport": "RTP/AVP/TCP;interleaved=0-1;ssrc=43f91496;mode=\"play\"", "date": "Sat, Jan 18 2020 01:43:29 GMT" } 2020-01-22T20:43:46.287Z [DEBUG] [172.17.126.58:46646 <HJK-NVLWI>] [CLIENT RESPONSE] <-- [200 (OK)] <cseq=2> (session=1653669771;timeout=20) 2020-01-22T20:43:46.289Z [TRACE] [172.17.126.58:46646 <HJK-NVLWI>] [CLIENT RESPONSE] <-- [HEADERS] { "cseq": "2", "session": "1653669771;timeout=20", "transport": "RTP/AVP/TCP;interleaved=0-1;ssrc=43f91496;mode=\"play\"", "date": "Sat, Jan 18 2020 01:43:29 GMT" } 2020-01-22T20:43:46.334Z [DEBUG] [172.17.126.58:46646 <HJK-NVLWI>] [CLIENT REQUEST] --> [PLAY] rtsp://172.17.126.25:554/ 2020-01-22T20:43:46.336Z [TRACE] [172.17.126.58:46646 <HJK-NVLWI>] [CLIENT REQUEST] --> [HEADERS] { "session": "1653669771", "user-agent": "Fire OS/6.0 stagefright/1.2 (Linux;Android 7.1.2)", "cseq": "3" } 2020-01-22T20:43:46.345Z [DEBUG] [172.17.126.58:46646 <HJK-NVLWI>] [ENDPOINT REQUEST] --> [PLAY] rtsp://172.17.126.25:554/ 2020-01-22T20:43:46.349Z [TRACE] [172.17.126.58:46646 <HJK-NVLWI>] [ENDPOINT REQUEST] --> [HEADERS] { "session": "1653669771", "user-agent": "Fire OS/6.0 stagefright/1.2 (Linux;Android 7.1.2)", "cseq": "3", "authorization": "Digest username=\"admin\", realm=\"f84dfc9a436b\", nonce=\"9a262528de6debf634b0858eec3f13bc\", uri=\"rtsp://172.17.126.25:554/\", response=\"4691f39f5927c8f5edacd750bc1b42c2\"" } 2020-01-22T20:43:46.443Z [DEBUG] [172.17.126.58:46646 <HJK-NVLWI>] [ENDPOINT RESPONSE] <-- [200 (OK)] <cseq=3> (session=1653669771) 2020-01-22T20:43:46.447Z [TRACE] [172.17.126.58:46646 <HJK-NVLWI>] [ENDPOINT RESPONSE] <-- [HEADERS] { "cseq": "3", "session": "1653669771", "rtp-info": "url=rtsp://172.17.126.25:554/trackID=1;seq=21883;rtptime=2033712161", "date": "Sat, Jan 18 2020 01:43:29 GMT" } 2020-01-22T20:43:46.453Z [DEBUG] [172.17.126.58:46646 <HJK-NVLWI>] [CLIENT RESPONSE] <-- [200 (OK)] <cseq=3> (session=1653669771) 2020-01-22T20:43:46.455Z [TRACE] [172.17.126.58:46646 <HJK-NVLWI>] [CLIENT RESPONSE] <-- [HEADERS] { "cseq": "3", "session": "1653669771", "rtp-info": "url=rtsp://172.17.126.25:554/trackID=1;seq=21883;rtptime=2033712161", "date": "Sat, Jan 18 2020 01:43:29 GMT" } 2020-01-22T20:43:46.461Z [INFO] [172.17.126.58:46646 <HJK-NVLWI>] RTSP ENDPOINT PLAYING MEDIA STREAM: Doorbell (STREAM:314be7ee-cb79-440a-8b73-558d4d9e3c36) 2020-01-22T20:43:46.465Z [INFO] [172.17.126.58:46646 <HJK-NVLWI>] RTSP CLIENT PLAYING MEDIA STREAM: Doorbell (STREAM:314be7ee-cb79-440a-8b73-558d4d9e3c36) 2020-01-22T20:44:05.631Z [INFO] [172.17.126.58:46646 <HJK-NVLWI>] RTSP CLIENT SOCKET CLOSED 2020-01-22T20:44:05.635Z [INFO] [172.17.126.58:46646 <HJK-NVLWI>] RTSP CLIENT DETACHED FROM STREAM: Doorbell (STREAM:314be7ee-cb79-440a-8b73-558d4d9e3c36) 2020-01-22T20:44:05.641Z [INFO] [172.17.126.58:46646 <HJK-NVLWI>] RTSP ENDPOINT SOCKET CLOSED [172.17.126.58:46646 <HJK-NVLWI>] -
Glad it’s working. I was trying to get my doorbell cameras to work last weekend and stumbled across this command reading the forums. The response time you show in your video is also about the same for me. Somewhat slower than my other cameras on the Monocle gateway. Perhaps some improvements may be coming soon?
-
@ScottR-LA Hey Scott did you say you have this working with FireTV stick as well?
-
If using the tags @fakefmtp @tunnel can somebody confirm this now works with the original DB1 and not just the DB2
Thanks