Unknowed brand IPcam
-
@Tueftler said in Unknowed brand IPcam:
OK, look like the Monocle Gateway is listening on port 443, not getting blocked by a firewall and you are able to successfully make an external connection to it and obtain its SSL certificate. All looks good.
So the last thing that is really left is the actual Amazon Alexa devices. Are you sure they are on the same network with access to the Monocle Gateway? Not on a guest or isolated network/VLAN? Unfortunately the Alexa devices are a bit of a black box and we have no way to really know if they are attempting the connection and why they might be failing. We seem to have verified any potential roadblocks that would prevent them from connecting. I fear the only options left are to packet sniff the network and see the traffic between the Alexa device and the Monocle Gateway to see if there is any attempts from Alexa. Does your Fritzbox provide any means for sniffing or packet capture? I use a PFSense router in my environment and there are add-ons that allow me to capture traffic and inspect it.
I know other users with Fritzbox have had issues with DNS REBINDING, but that does not seem to be a problem in this case because you are able to connect via the DNS hostname.
Thanks, Robert
-
I must read it again to understand all, because I am German and my technical Englisch is not the best.
I have installed a terminal on my mobile phone and made the test again via VPN
The result is this
openssl s_client -showcerts -connect 9dd28fe1-40f2-4459-805d-daa62fdc6ff5.mproxy.io:443 527989941576:error:2008F002:BIO routines:BIO_lookup_ex:system lib:crypto/bio/b_addr.c:710:No address associated with hostname connect:errno=0 $ -
Alexa, my Laptop and all other device in same Network Alexa and the Laptop also with the same SSID only the IP Cam is on a second Fritzbox with other SSID but they all in same Network.
I don’t now if there is a way to record network traffic on the Fritzbox.
-
The DNS hostname resolves to your local/private IP address.
> nslookup 9dd28fe1-40f2-4459-805d-daa62fdc6ff5.mproxy.io Server: 10.1.1.1 Address: 10.1.1.1#53 Non-authoritative answer: Name: 9dd28fe1-40f2-4459-805d-daa62fdc6ff5.mproxy.io Address: 192.168.2.87So if you are testing it over the Internet, it will certainly fail. However, if you are testing over VPN, it should work assuming that your Fritzbox is properly allowing nodes to resolve the local IP address from the DNS hostname. I think the Fritzbox by default will BLOCK this as a DNS REBINDING attempt. Basically some routers like the Fritzbox won’t allow public DNS hostnames to resolve to private IP address on your network – as this could be considered a threat to your network. However in our case, Amazon only allows their Alexa devices to connect to publicly resolvable DNS hostnames – but they can resolve to private addresses. There is nothing technically wrong with doing this, but some routers see this as a potential vulnerability and block these type of DNS queries.
Its best to perform the PING tests and the OPENSSL test command from another computer on your local network separate from the computer running the Monocle Gateway (or from a computer or device connected via VPN should be fine?).
Thanks, Robert
-
so now i have installed the Monocle Gateway on my Raspberry pi, this is running 24/7
now i can made the tests with the laptopIf i Test i become the same output in log:
Jul 17 14:57:40 FhemServer monocle-gateway[27235]: INITIALIZE RTSP STREAM: test2 Jul 17 14:57:40 FhemServer monocle-gateway[27235]: ------------------------------------------------- Jul 17 14:57:40 FhemServer monocle-gateway[27235]: - NAME : test2 Jul 17 14:57:40 FhemServer monocle-gateway[27235]: - LABEL : PRIMARY Jul 17 14:57:40 FhemServer monocle-gateway[27235]: - URL : rtsp://192.168.2.102:554/user=admin&password=marokaner1510&channel=1&stream=1.sdp Jul 17 14:57:40 FhemServer monocle-gateway[27235]: - UUID : STREAM:7d8ddf5b-a0b3-45ff-b203-a7d1f4070cfc Jul 17 14:57:40 FhemServer monocle-gateway[27235]: - SESS : dc987c54-8fdf-4c2c-8f47-324577513814 Jul 17 14:57:40 FhemServer monocle-gateway[27235]: - MODIF : Tue Jul 16 2019 10:45:15 GMT+0200 (CEST) Jul 17 14:57:40 FhemServer monocle-gateway[27235]: - TAGS : @fixaudio,@tunnel Jul 17 14:57:40 FhemServer monocle-gateway[27235]: -------------------------------------------------i have installed openssl on the laptop by downloading the setup.exe and installing but in the commandpromt comes the messages that openssl is wrong or can not be found
openssl s_client -showcerts -connect 9dd28fe1-40f2-4459-805d-daa62fdc6ff5.mproxy.io:443Edit: the ping test to the raspberry looks good:
C:\>ping 9dd28fe1-40f2-4459-805d-daa62fdc6ff5.mproxy.io Ping wird ausgeführt für 9dd28fe1-40f2-4459-805d-daa62fdc6ff5.mproxy.io [192.168 .2.172] mit 32 Bytes Daten: Antwort von 192.168.2.172: Bytes=32 Zeit=5ms TTL=64 Antwort von 192.168.2.172: Bytes=32 Zeit=2ms TTL=64 Antwort von 192.168.2.172: Bytes=32 Zeit=3ms TTL=64 Antwort von 192.168.2.172: Bytes=32 Zeit=2ms TTL=64 Ping-Statistik für 192.168.2.172: Pakete: Gesendet = 4, Empfangen = 4, Verloren = 0 (0% Verlust), Ca. Zeitangaben in Millisek.: Minimum = 2ms, Maximum = 5ms, Mittelwert = 3msso what can i do
-
On Windows, since the installer did not include the “openssl.exe” in your path by default, you can change directories at the command prompt before running the test using the first command below:
cd "\Program Files (x86)\GnuWin32\bin" openssl s_client -showcerts -connect 9dd28fe1-40f2-4459-805d-daa62fdc6ff5.mproxy.io:443The successful ping test tells us that the DNS should be working and resolving properly on your network – so in theory, DNS REBINDING should not be a problem.
So I suspect this
opensslcommand test will be successful as well. Lets go ahead and verify it just to make sure. This will further verify that we can in fact access port 443 and get a valid SSL certificate response.Thanks, Robert
-
Okay here the result:
Server certificate subject=/CN=*.mproxy.io issuer=/C=US/O=Let's Encrypt/CN=Let's Encrypt Authority X3 --- No client certificate CA names sent --- SSL handshake has read 29777 bytes and written 450 bytes --- New, TLSv1/SSLv3, Cipher is AES256-SHA Server public key is 2048 bit Compression: NONE Expansion: NONE SSL-Session: Protocol : TLSv1 Cipher : AES256-SHA Session-ID: 5B7776799F28F9049A80093118EFDBCBC314C1408FCC8382D96CCD26D79F7B4E Session-ID-ctx: Master-Key: 1AB19413C57A5FB7ECEB0883D2111B09C96C163B86B40A82803E2F7AB16ECAAE 3CD9279FECAC3C6C780226225177105E Key-Arg : None Start Time: 1563460616 Timeout : 300 (sec) Verify return code: 20 (unable to get local issuer certificate) --- closedi have not copied the part with all the certifikate
-
must the Port 443 linked in my Router to the Server where Monocle Gateway is running?
so Portforwarting port 443 to 192.168.2.172? -
No … no port forwarding should be necessary.
So all this is getting to be pretty strange. It looks like your gateway and network are perfectly fine, but for some reason Alexa simply will not even attempt to connect. Unfortunately Alexa does not provide any logging or diagnostics available to us to know if she is even attempting the connection or why it might be failing.
Do you know how to do network packet sniffing or have a router that can capture the traffic out from the Alexa device?
What country are you located in? Just trying to determine if this could be a regional issue.
Let me think on this and see what steps might help shed further light on this.
Thanks, Robert
-
I am from Germany, so is the reason my english is not the best.
can we do anything with wireshark? i have seen it but not used befor.
-
Yes, you should be able to use WireShark to capture data over the network. It’s been several years since I have used it so not sure what all the requirements are, but you may need a network adapter that supports promiscuous mode to see all the traffic. You might also check into the support for your router. I know that I can analyze traffic using my PFSense router. What we would be looking for is any TCP traffic originating from the Alexa device to the host computer running the Monocle Gateway on port 443. Or potentially any DNS requests attempting to resolve your gateway’s host record “*.mproxy.io” coming from the Alexa device.
In the meantime, I think I will try to setup a public testing camera or video feed that you can also try to use. It may take me a few days to get it up as I am traveling. This could at least allow us to verify the Alexa device is connecting to a resource over the cloud and verify the SSL certificates, etc.
Thanks, Robert
-
After thinking a bit further, I’m not sure WireShark alone can get to the information needed. The Alexa device will be connecting to your WiFi router and in between the WiFi and your other computer/laptop the traffic is likely going over a switched network which means the computer/laptop running WireShark may not be able to see the traffic coming from Alexa. So this may be a bit more involved to capture this data.
-
Sorry I repeat do late, I have tester with Wireshark but I don’t now to use it.
My last idea is to take a not used Raspberry Pi as bridge between Alexa and my rooter and there install a network Swiffer bekause my Fritzbox from Unitymedia have disabled the network monitor tool.
Or did you have a other idea?
-
So I have connected Alexa with a other Fritzbox, Ther i can record the network traffic. After starting record I have tester to show the 3 device Garten, test1 and test2, then I have stopped the record.
In the attachment is the record file I hope it helpsi can not upload the file, not privileges
-
I sent a PM to you via the chat on this forum site for additional follow up.
Thanks, Robert
-
OK, here is a test feed to try with your Echo Show (Gen 1).
This first test does not require any tags.
Here is the RTSP URL:
rtsp://demo.mproxy.io:443/resortHere it is configured in my camera settings in the Monocle Web Portal:
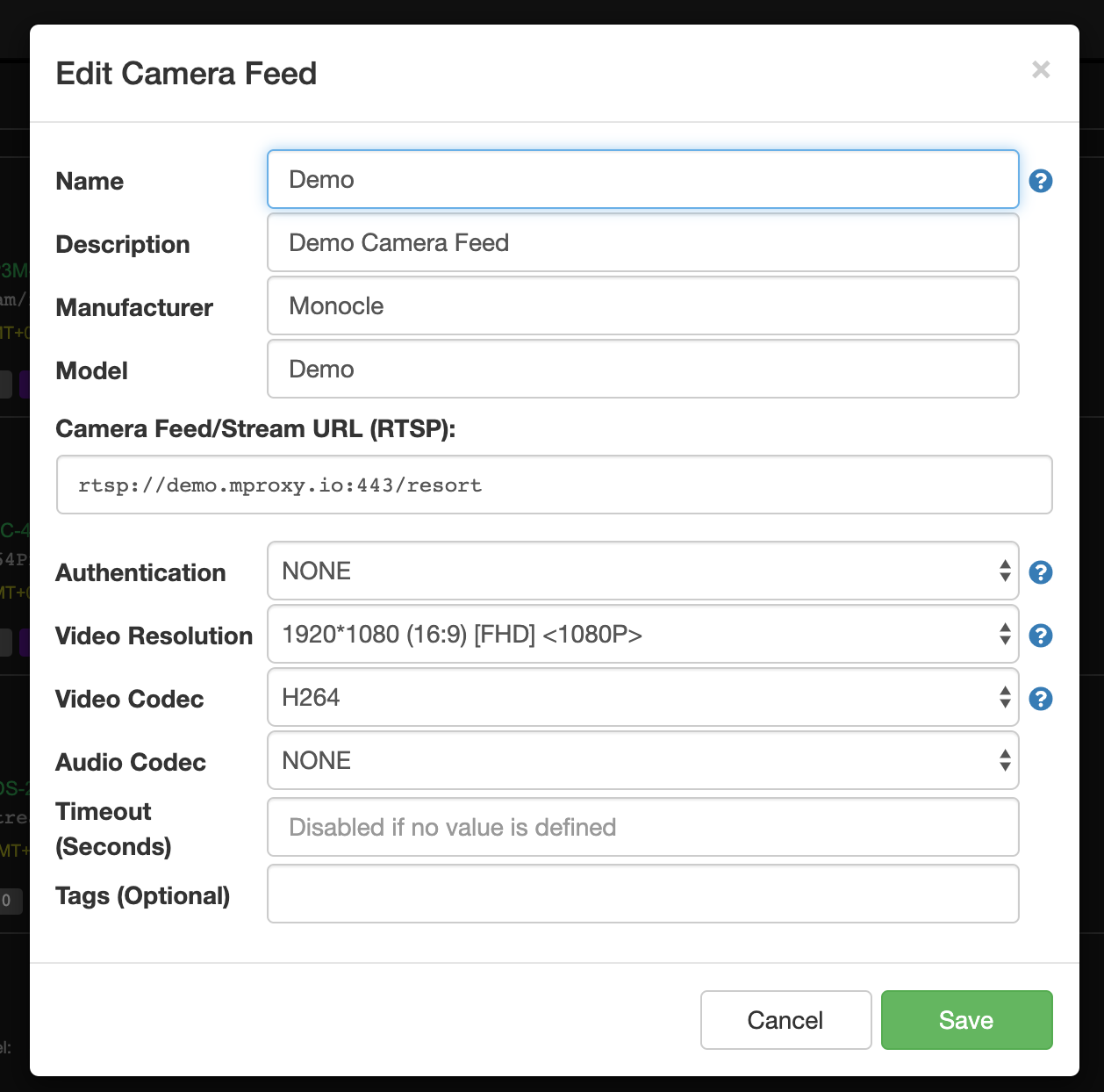
This will at least test the SSL certificates and certification chain to make sure that is not the problem.
Thanks, Robert
-
Hallo i have send you the E-mail with the network log.
Also i have testet the Camera demo you give to me and this works.
-
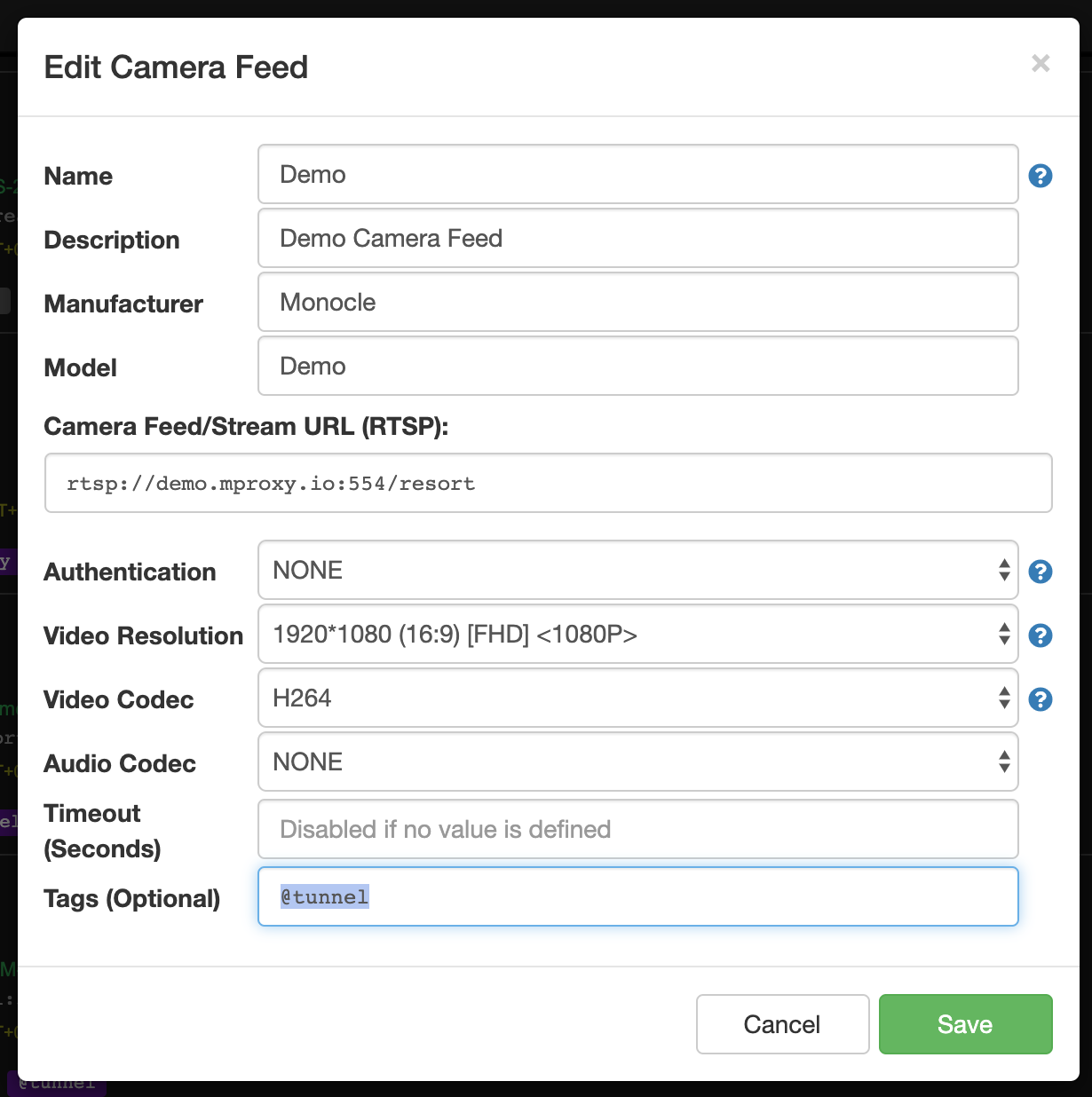
if i use the tag @tunnel in your demo Camera, the cam is not Working is this normal?
-
or is the Problem the Audio Code??
-
if i use the tag @tunnel in your demo Camera, the cam is not Working is this normal?
OK, the next test will involve running the same demo feed thru your instance of Monocle Gateway. However, I had to fix a couple of minor issues to get it working.
So, first. You will need to replace your “
monocle-gateway.exe” file with a newly compiled one from this link:
https://www.dropbox.com/sh/m91e8z2wa1s89d7/AACRqcwLvdTFA-5gsBo9ItrKa?dl=0&lst=(The new version should be “0.0.4-1” instead of “0.0.4”)
Now, we will need to update the demo RTSP URL to use port 554 instead of 443. Port 443 is already encrypted whereas port 554 is the raw unencrypted feed.
rtsp://demo.mproxy.io:554/resortYou will also need to add the
@tunneltag to the camera config as shown below: